Table of Contents
ToggleHow to Design Smarter Access Control for Your Business
In today’s complex security landscape, controlling who can open a door is no longer enough. Modern access control depends on structured permission management — clearly defined access levels.
Whether you’re protecting sensitive business assets, securing residential properties, or managing multi-tenant buildings, access levels form the foundation of a scalable and reliable security strategy. This guide explains what access levels are, how they work, and how to design them effectively for real-world business environments.

What Access Levels Mean in Modern Access Control
An access level is a core logical unit within an access control system. It’s not a single door and not an individual user. Instead, it’s a permission template that links specific locations with defined time schedules.
Its primary purpose is to simplify permission management. By grouping users with similar access needs — such as departments, roles, or shifts — administrators can assign permissions accurately and at scale, without managing each door and user individually.
Think of access levels like an organizational chart. Each role — manager, staff member, contractor, visitor — carries a predefined scope of access. When a new employee joins, assigning the correct role automatically applies the right permissions. This reduces setup time and limits access errors, which is especially valuable for small teams with limited IT resources.
From Physical Keys to Digital Permissions
Traditional mechanical master key systems represent an early form of access levels. User keys, master keys, and grand master keys defined physical access hierarchies through hardware.
Modern electronic access control systems digitize this concept. Permissions become flexible, traceable, and easier to adjust as teams grow or change — far beyond what physical keys can offer.
With more than a decade of experience in lock manufacturing, EOS SECURE understands this evolution deeply. Our mechanical and electronic lock solutions are designed to support both traditional key hierarchies and modern digital access frameworks, enabling a smooth transition between physical and electronic security models.
How Access Levels Fit Into Access Control Models
Access levels are typically implemented using one or more established access control models.
DAC — Flexible but Harder to Control
In DAC systems, the resource owner determines access permissions. This model offers flexibility but relies heavily on individual judgment, which can lead to inconsistent access decisions.
Best suited for small teams where simplicity matters more than strict enforcement.
MAC — Strict Control for High-Security Environments
MAC systems enforce centrally defined policies. Users cannot change permissions, and access decisions are based on strict classifications.
Best suited for government, military, or high-security environments where consistency outweighs flexibility.
RBAC — The Most Practical Model for Businesses
RBAC assigns access based on organizational roles.
An access level effectively represents one or more role-based permissions. For example, an HR role might combine office access during business hours with restricted access to records storage.
RBAC simplifies administration and scales well as organizations grow or restructure. For many small and mid-sized businesses, it provides the best balance between control and ease of management.
ABAC — Dynamic Access Based on Context
ABAC evaluates multiple attributes — role, department, location, time, and context — to make access decisions. This allows fine-grained, dynamic control in complex environments.
EOS SECURE’s Practical Approach
Regardless of the model used, EOS SECURE provides hardware that executes these strategies reliably. From precision-engineered master key cylinders to electronic locks that integrate with RBAC or ABAC platforms, we ensure that security policies are enforced consistently at every door.
How to Design Access Levels That Actually Work
Designing access levels is an iterative process that balances security, usability, and operational efficiency.
Step 1 — Identify Who Needs Access and Where
- List all controlled entry points — doors, rooms, cabinets, and zones
- Interview stakeholders to understand daily workflows and access patterns
- Identify groups with similar access needs, such as night staff, contractors, or delivery personnel
Step 2 — Start With a Small Set of Access Levels
Start simple. Most organizations begin with three to five levels.
Examples include:
- General Staff – Business Hours
- Management – Full Access
- IT Staff – Server Rooms
- Cleaning Staff – After Hours
- Visitors – Temporary Access
This approach avoids overcomplication while still providing meaningful control.
Step 3 — Apply Access Levels in Your System
- Create access levels in the control software
- Assign doors and schedules to each level
- Assign users — allowing multiple access levels per user when needed
For example, a retail manager may need both general staff access and extended after-hours permissions.
Step 4 — Review, Test, and Adjust Over Time
- Validate permissions before full rollout
- Review access levels regularly as roles, staffing, or business hours change
What You Need to Make Access Levels Work in Practice
Effective access levels rely on both hardware and software working together.
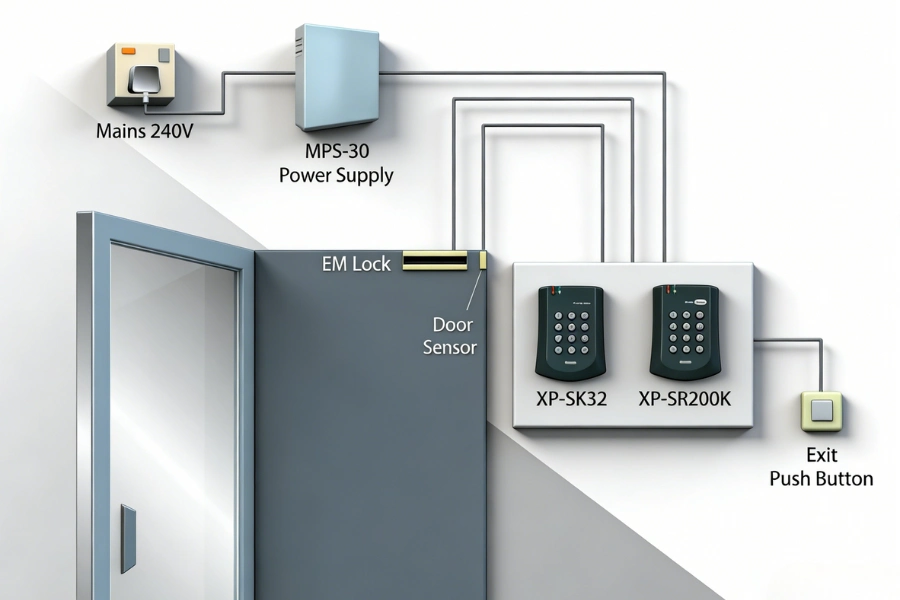
A Reliable Hardware Foundation
- Access control panels that process permission decisions
- Credential readers such as cards, PIN pads, or biometrics
- Door locking hardware that executes access commands
EOS SECURE plays a critical role at this layer. Our high-security electronic cylinders and smart lock assemblies are built for durability, resistance to attack, and seamless integration with leading access control platforms — ensuring every permission decision is enforced accurately.
Intelligent Management Software
- Centralized control of users, doors, and access levels
- Audit logs for compliance and accountability
- Remote and mobile management for flexibility
Scalability and System Integration
- Easy expansion as facilities or staff grow
- Integration with video surveillance, alarms, and emergency systems
Where Access Level Management Is Headed Next
Access management is becoming more adaptive.
AI-driven systems can detect abnormal patterns and adjust access rules dynamically. Advanced ABAC models enable context-aware decisions based on real-time conditions. These capabilities improve security without increasing administrative burden.
Why Access Levels Matter for Long-Term Security
Access levels represent the shift from basic door control to intelligent security management. When designed correctly, they enhance protection, simplify operations, and provide clear audit trails for compliance.
A well-structured access level strategy reflects how an organization actually works — and adapts as it grows.
EOS SECURE — Your Trusted Access Control Hardware Partner
EOS SECURE delivers precision-engineered mechanical and electronic lock cylinders backed by more than a decade of manufacturing expertise. Established in 2011, our factory operates under ISO9001 and ISO14001 certifications, ensuring every product meets rigorous international standards including EN1303 and SKG.
With advanced CNC manufacturing and flexible ODM and OEM capabilities, EOS SECURE supports both mechanical and electronic access strategies. Whether you’re deploying structured master key systems or integrating smart locks into modern access control platforms, we provide reliable hardware that helps businesses implement access levels with confidence and consistency.
Explore EOS SECURE solutions to see how the right hardware supports smarter access control decisions.
FAQ
What is an access level in access control systems?
An access level is a permission template that defines which doors or areas a user can access and during what time periods. Instead of managing access for each individual, businesses assign access levels to roles or groups. This approach simplifies administration, improves consistency, and reduces the risk of incorrect permissions.
What’s the difference between access levels and individual user permissions?
Access levels manage permissions in groups rather than individually. When an access level is updated, all users assigned to it are updated automatically. Individual permissions require manual changes for each user, which increases administrative workload and the risk of mistakes, especially as organizations grow or staff changes become more frequent.
How do you handle employees with multiple roles?
Modern access control systems allow a single user to hold multiple access levels at the same time. The system combines these permissions into one effective access profile. This is useful for employees who work across departments or shifts, ensuring they have appropriate access without creating complex or redundant permission settings.
How should temporary visitors be managed?
Temporary visitors should be assigned to time-limited access levels. These access levels grant entry only to specific areas and automatically expire after a defined period. This approach removes the need for manual access revocation, reduces security risks, and allows businesses to manage visitors, contractors, or short-term staff efficiently.
